Get to know the NIST Cybersecurity Framework
The Cybersecurity Framework or Cybersecurity Framework of the National Institute of Standards and Technology, NIST for its acronym in English, is a tool for managing risks associated with information security and although it is a framework of voluntary adoption, it offers different advantages . Here we tell you more about it.
What is the NIST Cybersecurity Framework and what is it for?
For some years, information security or cybersecurity has become more relevant in organizations, so much so that they have designed and executed programs to protect their information, their most important asset, and to act in the best way against a cyber attack because As with financial or reputational risks, cyber risk generates a negative impact on business objectives. With software like Pirani ISMS Suite you can easily identify, manage and control these risks.
Faced with this, there are different international standards that offer good practices for the implementation of an information security management system. The ISO 27001 standard is one of the best known, but not the only one.
In fact, the Cybersecurity Framework of the National Institute of Standards and Technology (NIST), which depends on the United States Department of Commerce, was developed taking into account the controls and processes presented by already accepted cybersecurity standards, among these: NIST SP 800-53, ISO/IEC 27001:2013, COBIT 5 and CIS CSC. Version 1.0 of the Framework was published in February 2014 and version 1.1 in April 2018.
As NIST itself explains, the Framework “is a methodology with an approach to reduce the risk associated with cyber threats that may compromise information security.”
And what is it for? The NIST Framework, which, due to its simplicity and flexibility, adapts to organizations of any sector or size, allows it to understand, manage and reduce the probability of a cyber risk occurring thanks to the adequate protection of its networks and data.
It can be used as a reference to establish a cybersecurity program or system or to review and identify opportunities to help complement and improve the existing one.
How is the NIST Cybersecurity Framework composed?
This Framework, also known as the Cybersecurity Framework, is made up of three parts: the core, the implementation levels, and the Framework profiles.
1. The core
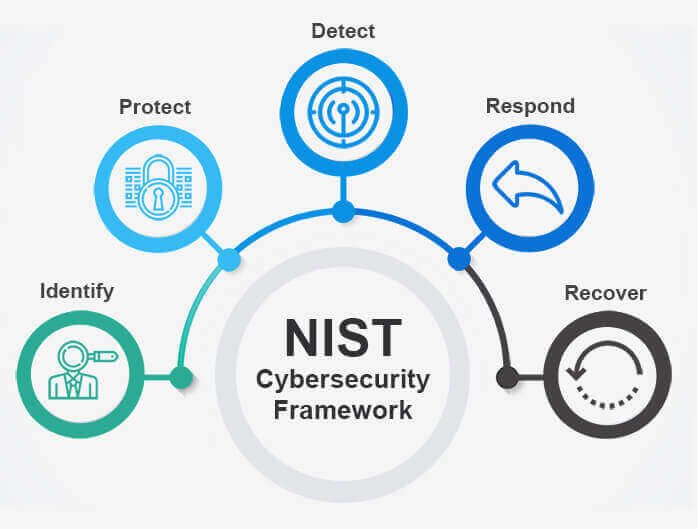
It is a set of activities to achieve cybersecurity results, it refers to industry standards, guidelines and good practices. This core is made up of five simultaneous and continuous functions that must be followed to implement or complement a good information security program.
These functions are:
In addition to these five functions, the core of the Framework is made up of three other elements: categories, subcategories and informative references; everyone works together to manage the risks associated with information security.
2. Framework Implementation Levels
Provide context for how an organization views cybersecurity risk and the processes and programs to manage it.
NIST’s selection of these levels takes into account risk management practices, legal and regulatory requirements, business goals, cybersecurity requirements, and more.
As he explains, “the levels support organizational decision-making on how to manage cybersecurity risk, as well as which dimensions of the organization are of higher priority and could receive additional resources.”
There are four levels and they are defined by the risk management process, the integrated risk management program and external participation:
To determine the desired level, NIST recommends that organizations ensure that the level they select meets their goals, is easy to implement, and reduces cyber risk to their assets and data.
3. Framework Profiles
Refers to the alignment of roles, categories, and subcategories with business requirements, risk tolerance, and organizational goals.
These profiles serve to describe the current or objective state of the activities carried out in cybersecurity. The current profile speaks of the results that are being achieved, while the target profile shows the results that are required to achieve the objectives outlined in cyber risk management.
How can you use the NITS Cybersecurity Framework in your company?
- As we have mentioned, this Framework is adaptable to organizations of any sector, country and size, and can be used in different ways: Review and compare the existing cybersecurity practices within the organization with those presented in the core of the Framework to see if expected results are being achieved and determine what things should or can be improved to further reduce cybersecurity risk.
Create a new cybersecurity program or improve an existing one. The Framework proposes the following steps to do so: - Prioritize and Scoping: Identify business goals and high-level priorities to make decisions regarding the scope of the cybersecurity program.
- Guidance: Identify systems and assets related to the scope of the program, regulatory requirements, and overall risk approach.
- Create a Current Profile: Develop a current profile to see what results by category and subcategory of the core Framework are being achieved.
- Conduct a risk assessment: analyze the environment to understand the probability of an event occurring
- Create an objective profile: this profile focuses on the evaluation of the categories and subcategories of the core of the Framework that indicate the results expected by the organization.
- Determine, analyze and prioritize gaps: compare the current profile and the target profile to see what the gaps are and create an action plan to address them and be able to achieve the expected results of the target profile. In addition, the funds and personnel required to fill these gaps must be determined.
- Implement the action plan: finally, implement the action plan and adjust the cybersecurity practices to achieve the target profile.
Other ways the NIST Framework can be used is to communicate cybersecurity requirements to stakeholders or make purchasing decisions about information-related products and services.As you have seen throughout this article, the NIST Cybersecurity Framework is another of the valid options that exist to implement adequate programs in organizations to manage and guarantee information security. Did you already know this Framework? Tell us what you thought and what other cybersecurity topics you would like to know more about.