Wi-Fi Security and Privacy: Suggestions for Victim and Survivor Services Agencies

WiFi access has become so common that many public places have networks and access points that you can connect to. But, just because a network is available does not mean that it is secure. The information below will provide you, and the survivors you serve, the tools you need to stay safe while using any WiFi network.
How WiFi Works
The following is a basic explanation of the various steps of WiFi communication:
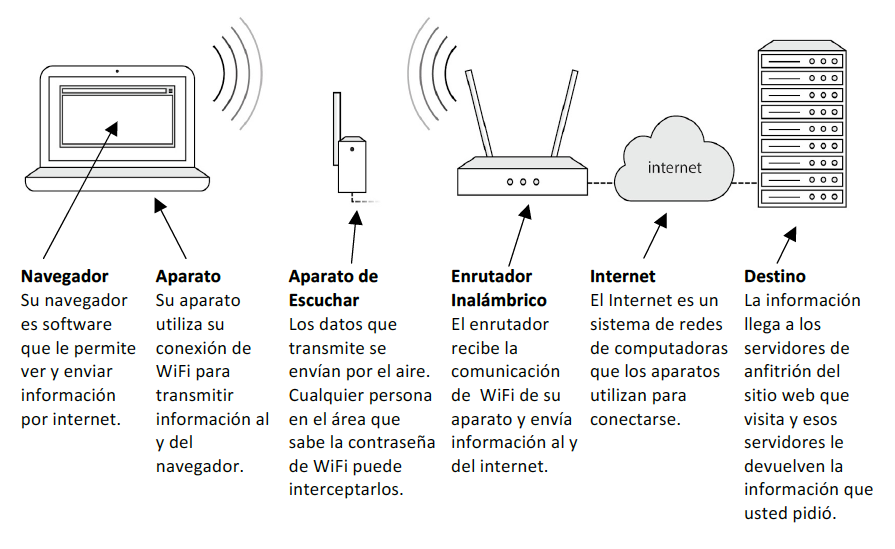
THE WIFI HOT SPOTS YOU CONTROL
A WiFi hotspot or “Hotspot” in English you can control has the ability to be as secure as a wired connection. To achieve this level of security, the following steps must be taken:
1. Use a Strong and Private Password
Choose a WiFi password that is long. The best passwords are at least 12-15 characters long and contain randomly placed letters, numbers, and symbols. Read more about Password Security . Do not pass out this password or write it in any conspicuous place (including on or near the hot spot itself).
2. Change Security Settings
Proper configuration will ensure that your WiFi Hotspot only supports the most up-to-date protocols for transmitting information:
- The only algorithm that must be enabled is WPA2. Disable WEP and WPA.
- The only encryption method that must be enabled is AES. Disable any settings related to TKIP.
- Disable WPS completely. This service is activated by default in most of the Hot Spots. It allows another method of connecting without a password. It has a significant security flaw that is easy to exploit.
3. Establish a Guest Network (optional)
Establish an alternate network if you have guests who need access to your internet connection. The password for this network does not have to be so complex or private. The name for the network should not be identifiable, for your privacy and for your guests.
The steps to access and configure a WiFi Hot Spot are different for each device. You may need the help of someone with experience to make these changes.
Open / Public WiFi Hot Spots
If you have serious privacy concerns or risks, it is critical to understand how to safely use a public / open WiFi network and when to avoid it. Any WiFi Hot Spot where there is no password or the password is available to the public should be considered an open network (a typical example of this is in a hotel where all guests have the same password and it is not changed frequently). Even if the network is password protected, someone with eavesdropping knowledge will still be able to see your communications if they also have access to the password.
There are two ways that you can safely surf the internet when using a public WiFi Hot Spot:
Use HTTPS
HTTPS adds an almost impenetrable level of encryption between your browser and the website you communicate with. Yes , sites that use an HTTPS connection can be trusted, even when using an open / public WiFi network. But, you should always check that there is “https” at the beginning of the web address and verify that the domain name is exactly the site you want. Saving important websites as bookmarks and always going to those websites using those bookmarks is a great way to make sure you don’t get tricked into going to a site that is not what it appears to be. You should always pay attention to the warnings that your browser gives you about problems with the security certificate of a website with HTTPS.
It is also important to remember that as long as the content of your HTTPS communications is private, the destination is not. Imagine that you have mailed a letter to a friend using a language that only you understand, but the address on the envelope is written in a language that everyone understands. Anyone who intercepts this letter not be able to read the message inside but themselves can see who is communicating reading the envelope. The same concept applies to network communications.
Activities that are generally safe when using HTTPS:
The web address or destination is typically not a secret; but, HTTPS can be relied upon to protect content from:
- Bank transactions or online purchases
- Web-based email (Gmail, Yahoo! Mail, etc.)
- Social networks (Facebook, Instagram, etc.)
- Any other service on the network that requires a username and password to view the information
Activities that are NOT private with HTTPS:
The information in the web address (the destination) reveals the information read
- Search engines (Google, Bing, etc.)
- Online maps (Google Maps, MapQuest, etc.)
- Any website that doesn’t want a eavesdropper to know that they have visited
The line between the “content” and the “destination” of a website can be blurred. When in doubt, always assume that your information is not private. Wait until you have an internet connection that you control before proceeding.
Use a Virtual Private Network (VPN)
An easy way to avoid almost all WiFi-related privacy risks is to subscribe to a virtual private network (VPN). A VPN will encrypt 100% of the traffic your computer sends and deliver it to an alternate server elsewhere on the internet. Once the information has reached the alternate server, it will be decrypted and sent to its final destination. The VPN makes it appear that the requests you sent came from that alternate server and keeps your IP address and location anonymous.
A VPN provides the following benefits:
- Encrypts all network traffic (HTTP and HTTPS) while traveling over WiFi
- Masks both the network content and the destination while traveling over WiFi
- It masks your original IP address of the website you visit. This prevents the website from tracking your IP address to your geographic area.
OTHER SAFETY TIPS
1. Keep the Software Updated
It is very important that you update your operating system, your browser, your anti-virus program and anything else on your computer, tablet or device related to the Internet or security soon. If you don’t update them, your computer will be vulnerable. New threats are always discovered, and these updates help protect against those threats, but only when they are the most recent versions. It can be helpful to think of upgrades as a roof with a hole – if you don’t fix it as soon as possible, things could become very serious soon and your roof could sag.
2. Use Anti-Virus / Anti-Spyware Software
Although not perfect, anti-virus / anti-spyware programs are still an important tool to stop malicious content before it reaches your browser.
Most computers already have anti-malware and anti-spyware applications installed. These applications are typically only free for an initial period and should not be relied upon after the expiration date. You can also download a variety of free anti-virus programs.
Anti-malware applications are available for cell phones, but they do not provide as many benefits as those for computers.
It is important to fully evaluate any anti-virus program before installing it. It is common for malware programs to disguise themselves as anti-virus programs or tools to scan your computer to trick you into installing them.
3. Use Privacy Screens
A low-tech way to prevent someone from looking over your shoulder to see the information on your devices is to use a privacy screen. Privacy screens are dark filters to put on top of your laptop or tablet screen to prevent someone from seeing what you are doing.
4. Manage your WiFi network history
Most mobile devices and computers store a list of the WiFi networks you have connected to. Review the list and remove any that are not safe to keep. You may not want to delete the entire list because that could raise suspicions from someone who physically controls your devices. Also, it might not be convenient to delete the entire list because it probably contains the WiFi network you connect to most frequently (including passwords).
WHAT SURVIVORS AND ADVOCATES CAN DO
For victims of domestic violence, stalking, and sexual assault and their advocates, there are some additional options to increase your safety.
1. Make Security Plans
For survivors of abuse, having safe access to the internet is important. It is important to make security plans about the use of technology and update those plans regularly. Share this information about Wi-Fi safety with survivors so they can make informed decisions about their internet use.
2. Know Your Devices
Most appliances have settings that increase security. Both advocates and survivors should know how to change, modify, and disable settings on their devices. For more information on the various device settings and capabilities, visit TechSafety.org .
3. Trust your Instincts
Always trust your instincts. If you think that a particular network, website, or service is unreliable, use caution when using it. If you need to use it, do not share confidential information while doing it.
TO SUM UP
The internet is a wonderful tool and survivors have the right to access information freely without fear for their safety. It is an important tool that allows survivors to feel empowered and independent. But, survivors and advocates need to be aware of the risks and know how to manage them. With these tips and strategies, both survivors and advocates can reduce the vulnerability of their devices and the risk that their devices and information will be compromised when using any WiFi network.
* Special thanks to Steven Jenkins of EmpowerDB for providing insight into this content. *






